ELISA
SECURITY MANAGER
CENTRAL OPERATIONAL AND SECURITY MONITORING
It is a robust and powerful, yet cost-effective solution for log collection, correlation and analysis. It meets the needs of most organizations and complies with the requirements of the Cyber Security Act.
We offer friendly
comprehensive security supervision
Security risk detection
Provides high comfort in the analysis of detected security incidents and relevant logs.
Continuous development according to current trends and customer needs
We keep abreast of current trends and customer requirements, which ensures the continuous development of our system.
Low acquisition costs
It is a very cost-effective LM / SIEM solution that meets the needs of most organizations.
News from world of logs
INTRODUCING ELISA 4.8
ELISA 4.8 is here with new interesting features that this update brings. ELISA still remains a robust, powerful, yet cost-effective solution for collecting and evaluating cyber security incidents....
INTRODUCING ELISA 4.7
ELISA 4.7 is here with new interesting features that this update brings. ELISA 4.7 still remains a robust, powerful, yet cost-effective solution for collecting and evaluating cyber security...
THE FIRST CZECH ZABBIX ONLINE MEETUP
CoreIT together with partners DATASYS, S.ICZ and TOTAL SERVICE invites you to the first Czech online Zabbix Meetup. You can look forward to the presentation of our colleague Lukáš Malý and other...
TOOL FOR INTERCEPTING AND EVALUATING
CYBERNETIC SECURITY EVENTS
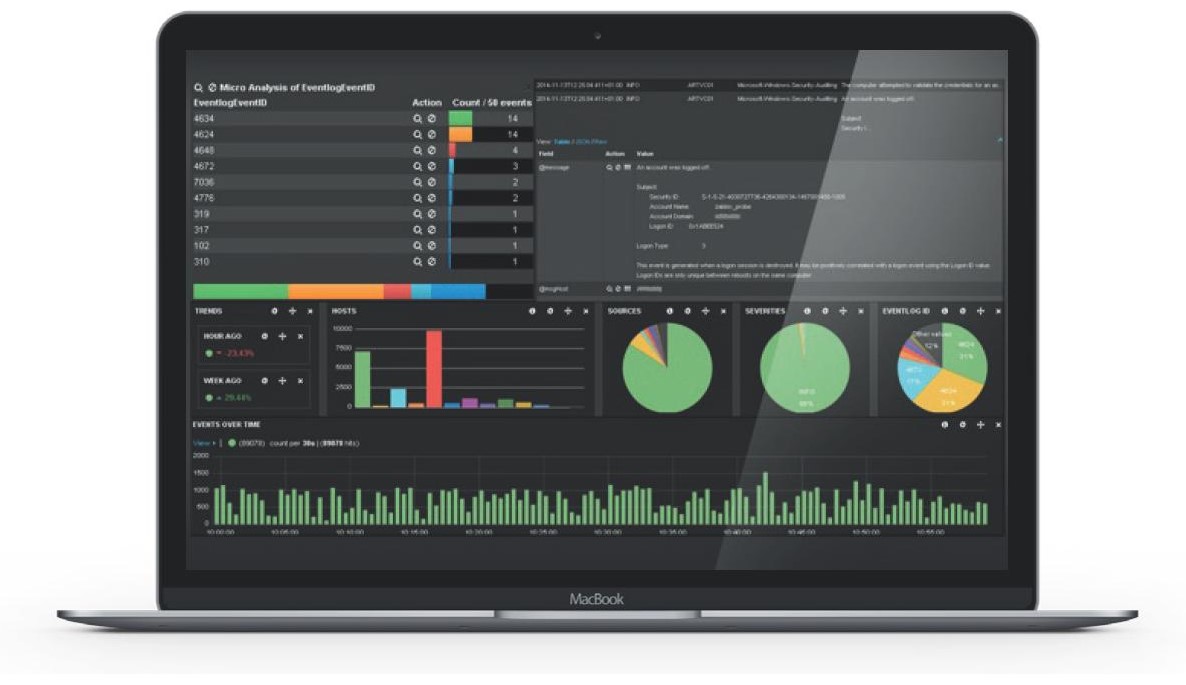
Searching the event database is similar to searching the Internet, simply by entering keywords. After a short training, even an inexperienced user can also formulate complex filters that far exceed the possibilities of searching in relational databases. Dividers can be saved for reuse.
It is common to distribute a database to multiple servers in order to share the load and high availability of indexed data. An integral part of ELISA is the globally widespread ZABBIX operational monitoring tool, the web interface which also includes settings for configuration of log collection and evaluation in ELISA.
KEY PROPERTIES
- Automatic evaluation.
- Security risk detection.
- A clear and simple web user interface.
- Compliance with the Cybersecurity Act, GDPR, ISO, PCI.
- Built-in Change Auditor.
- Further advanced SIEM functions.
- OpenVAS and GSM integration.
- Flowmon ADS integration.
- Physical and virtual appliances.
- Distributed log collection.
- Horizontal scalability.
- High performance (up to 10 000 EPS).
- Low initial costs.
The solution is suitable for medium and large companies, municipal authorities and other public institutions.
Security Information and Event Management
ELISA also utilises an advanced correlation engine supporting contextual correlation, even over periods of several months. This allows the detection of cybersecurity events, not only through repeated elementary incidents, but also the spread of hidden malware over a network or users signing into applications after several weeks of inactivity.
The ESM allows you to enrich the events with information from external sources and calculates a “risk score” for all events, allowing one to easily prioritise the steps needed to resolve alarms that appear. The EMS includes support for regular monitoring of configurations (the so-called Change Auditor) and other advanced SIEM functions.
What information can ELISA uncover?
WHAT EXCEPTIONS EXIST IN THE
COMPANY IS?
WHO MADE CHANGES
TO THE DATABASE?
WHO IS TRYING TO GUESS
SOMEONE’S PASSWORD?
WHO DELETED THE FILES
ON THE SHARED DRIVE?
FROM WHERE ARE PEOPLE ACCESSING YOUR
COMPANY WEBSITE?
WHICH USERS ARE DOWNLOADING THE MOST
DATA FROM THE WEB?
References overview






Contacts us
Are you interested in our offer?
We will provide you with a free independent consultation and present the solution to you.
CONSULTATION & DEVELOPMENT
DATASYS s.r.o.
Pavel Štros
+420 603 280 019
monitoring![]() datasys.cz
datasys.cz
SUPPORT
elisa![]() datasys.cz
datasys.cz
Support Policy



